基于 CertManager – MetalLB – Ingress – Harbor 企业级云原生镜像仓库
基于 CertManager - Let's encrypt - MetalLB - Ingress - Harbor 企业级云原生镜像仓库
-
Reference1(originality): https://zsnmwy.notion.site/Cert-manager-MetalLB-Ingress-Harbor-22e73935b65a4b9e9e2f7daf22ef723b
-
Reference2: certmanager+cloudflare+letsencrypt Issuing a free certificate
1. First look at the effect
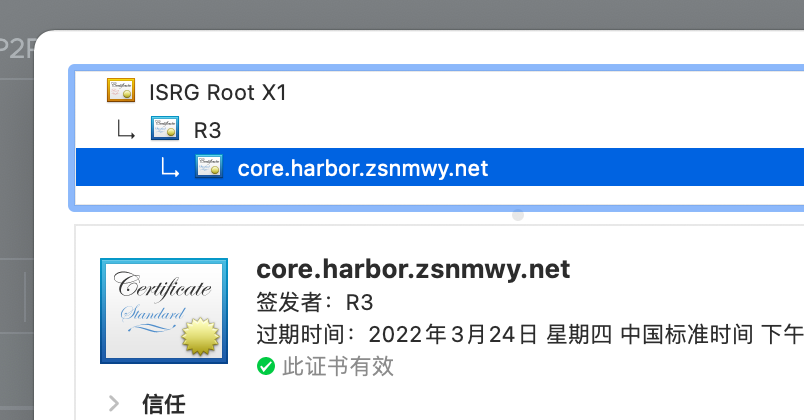
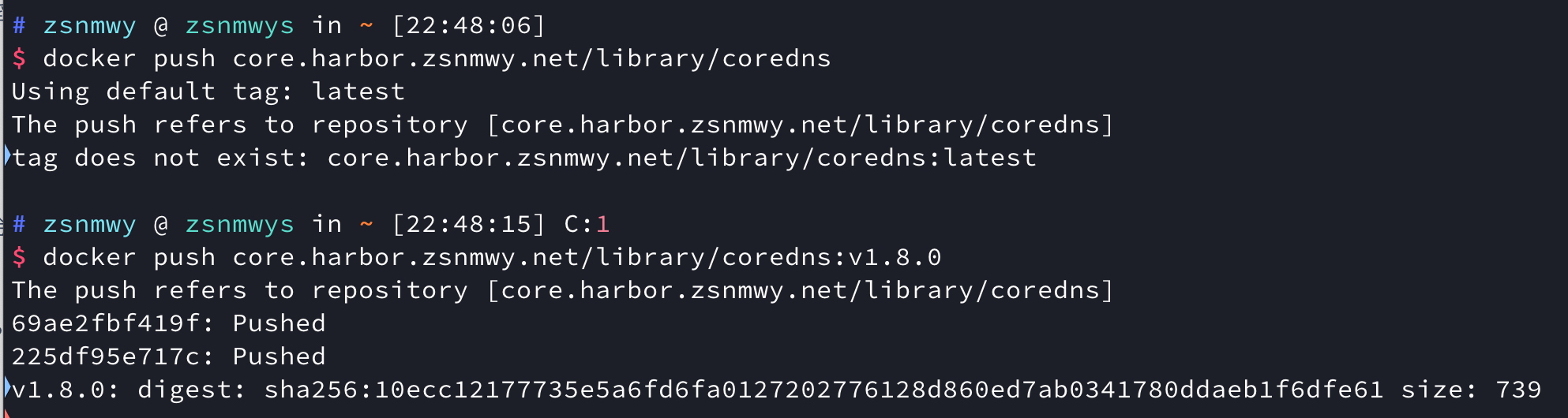
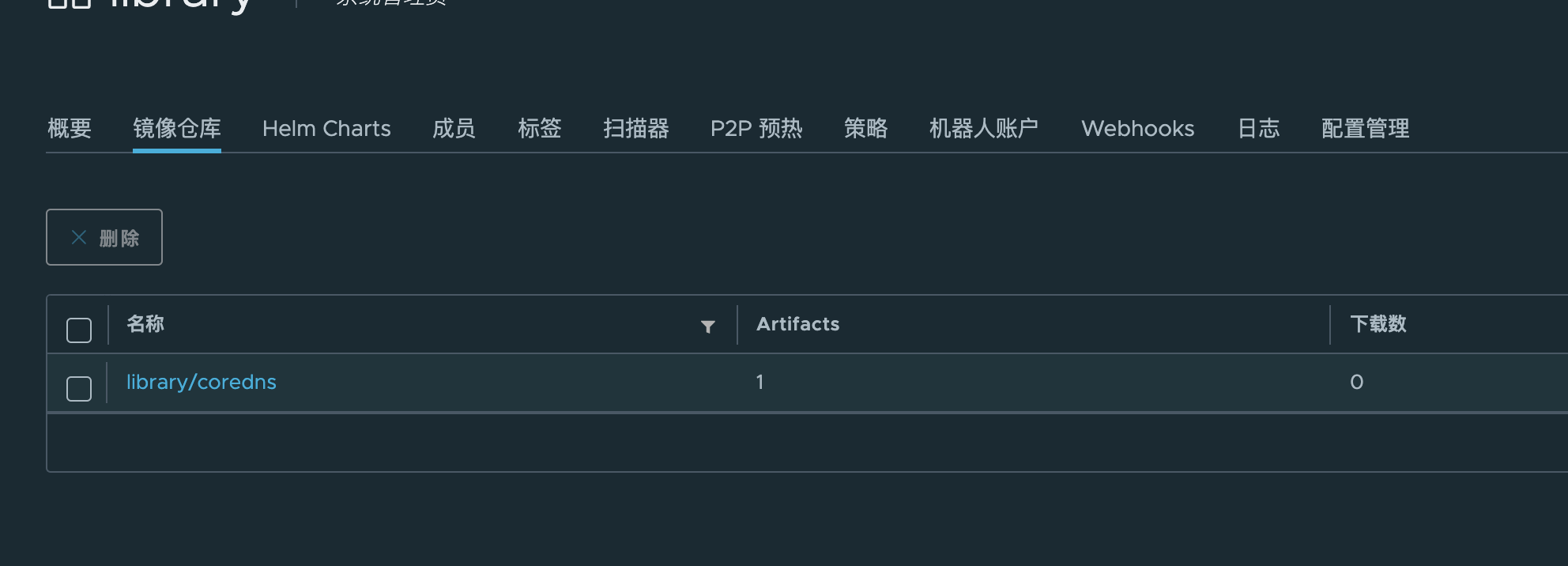
2. Deploy cert-manager
helm repo add jetstack https://charts.jetstack.io
helm repo update
# values ref https://artifacthub.io/packages/helm/cert-manager/cert-manager
# change what you want
helm install \
cert-manager jetstack/cert-manager \
--namespace cert-manager \
--create-namespace \
--version v1.6.1 \
--set prometheus.enabled=true \
--set webhook.timeoutSeconds=4 \
--set installCRDs=true- letsencrypt DNS auth
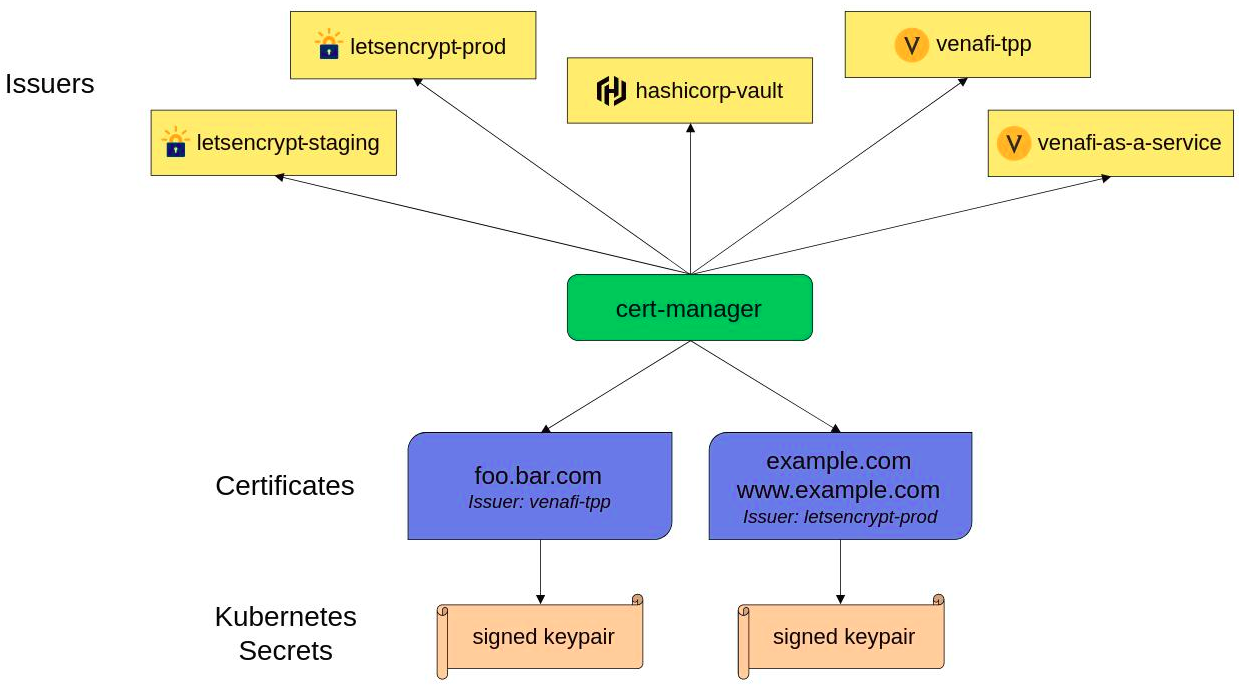
- Define cloudflare Issuer
cat <<EOF>cf-issuer.yaml
apiVersion: cert-manager.io/v1
kind: Issuer
metadata:
name: letsencrypt-prd
spec:
acme:
email: 983708408@qq.com
server: https://acme-v02.api.letsencrypt.org/directory
privateKeySecretRef:
name: letsencrypt-prd
solvers:
- dns01: # Choose DNS01 providers https://cert-manager.io/docs/configuration/acme/dns01/#supported-dns01-providers
cloudflare:
email: 983708408@qq.com
apiTokenSecretRef:
name: cloudflare-api-token-secret
key: api-token
EOF
k apply -f cf-issuer.yaml- Define cloudflare secret
cat <<EOF>cloudflare-api-token-secret.yaml
apiVersion: v1
kind: Secret
metadata:
name: cloudflare-api-token-secret
type: Opaque
stringData:
api-token: <cloudflare-api-token>
EOF
k apply -f cloudflare-api-token-secret.yaml- Define domain certificate
cat <<EOF>wl4g-certificate.yaml
apiVersion: cert-manager.io/v1
kind: Certificate
metadata:
name: wl4g-com # define certificate name
namespace: default
spec:
secretName: wl4g-com-tls #key pair will be store here
issuerRef:
name: letsencrypt-prd
dnsNames:
- '*.wl4g.com'
EOF
k apply -f wl4g-certificate.yaml$ k get certificate
NAME READY SECRET AGE
wl4g-com-tls True wl4g-com-tls 15h3. Auto create certificate by ingress
cat <<EOF>ingress-nginx.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: kuard
annotations:
kubernetes.io/ingress.class: "nginx"
cert-manager.io/issuer: "letsencrypt-prd" # Important !!!
spec:
tls:
- hosts:
- '*.wl4g.com' # Important !!!
secretName: wl4g-com-tls # Important !!!
rules:
- host: kuard.wl4g.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: kuard
port:
number: 80
EOF
k apply -f ingress-nginx.yaml4. Install ingress nginx
helm repo add ingress-nginx https://kubernetes.github.io/ingress-nginx
helm repo update
helm install ingress-nginx ingress-nginx/ingress-nginx -n ingress-nginx5. Deploy MetalLB (LoadBalancer)
-
MetalLB, bare metal load-balancer for Kubernetes
-
helm chart metallb values.yaml
cat <<EOF>values.yaml
configInline:
address-pools:
- name: default
protocol: layer2
addresses:
- 198.51.100.0/24 # CIDR
EOF- or
cat <<EOF>values.yaml
configInline:
address-pools:
- name: default
protocol: layer2
addresses:
- 192.168.1.240-192.168.1.250 # OR Range
EOFhelm repo add metallb https://metallb.github.io/metallb
# By default
#helm install metallb metallb/metallb
helm install metallb metallb/metallb -f values.yaml- Check ingress nginx (
externalIP)
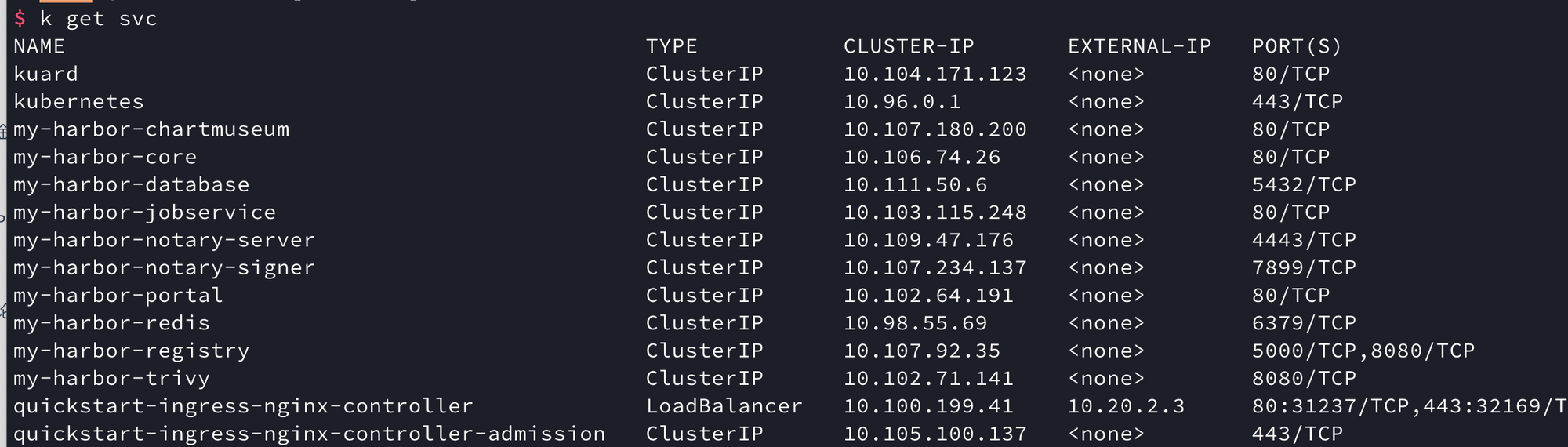
$ k get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kuard ClusterIP 10.104.171.123 <none> 80/TCP 16h
kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 10d
my-harbor-chartmuseum ClusterIP 10.107.180.200 <none> 80/TCP 12h
my-harbor-core ClusterIP 10.106.74.26 <none> 80/TCP 12h
my-harbor-database ClusterIP 10.111.50.6 <none> 5432/TCP 12h
my-harbor-jobservice ClusterIP 10.103.115.248 <none> 80/TCP 12h
my-harbor-notary-server ClusterIP 10.19.47.176 <none> 4443/TCP 12h
my-harbor-notary-signer ClusterIP 10.107.234.137 <none> 7899/TCP 12h
my-harbor-portal ClusterIP 10.102.64.191 <none> 80/TCP 12h
my-harbor-redis ClusterIP 10.98.55.69 <none> 6379/TCP 12h
my-harbor-registry ClusterIP 10.107.92.35 <none> 5000/TCP,8080/TCP 12h
my-harbor-trivy ClusterIP 10.102.71.141 <none> 8080/TCP 12h
quickstart-ingress-nginx-controller LoadBalancer 10.100.199.41 10.20.2.3 80:31237/TCP,443:32169/TCP 38h
quickstart-ingress-nginx-controller-admission ClusterIP 10.105.100.137 <none> 443/TCP 38h6. Deploy harbor
# Download Chat
helm repo add harbor https://helm.goharbor.io
helm fetch harbor/harbor --untar- helm chart
harbor/values.yaml
expose:
type: ingress
# Ingress nginx confiugration
ingress:
hosts:
core: core.harbor.wl4g.com # your must change it
notary: notary.harbor.wl4g.com # your must change it
annotations:
ingress.kubernetes.io/ssl-redirect: "true"
ingress.kubernetes.io/proxy-body-size: "0"
nginx.ingress.kubernetes.io/ssl-redirect: "true"
nginx.ingress.kubernetes.io/proxy-body-size: "0"
cert-manager.io/issuer: "letsencrypt-prd" # choose issuer
kubernetes.io/ingress.class: nginx
tls:
enabled: true
certSource: secret
secret:
secretName: "harbor-core-tls"
notarySecretName: "harbor-notary-tls"
# The external URL for Harbor core service.
externalURL: "https://core.harbor.wl4g.com" # your must change it
# you can change it if you want
persistence:
enabled: falsecd ~/harbor
helm install my-harbor .
# Check it
k get pod -A
NAMESPACE NAME READY STATUS RESTARTS AGE
calico-apiserver calico-apiserver-5b68b6b54-tg5x9 1/1 Running 1 (55m ago) 10d
calico-apiserver calico-apiserver-5b68b6b54-xp48c 1/1 Running 2 (53m ago) 10d
calico-system calico-kube-controllers-59c45ff85c-flvmq 1/1 Running 2 (53m ago) 10d
calico-system calico-node-2zmwt 1/1 Running 2 (53m ago) 10d
calico-system calico-node-d67lk 1/1 Running 1 (55m ago) 10d
calico-system calico-typha-55cfb7944c-w6d76 1/1 Running 2 (54m ago) 10d
cert-manager cert-manager-665bb4776f-pvls5 1/1 Running 1 (55m ago) 44h
cert-manager cert-manager-cainjector-89487b959-x5qvr 1/1 Running 1 (55m ago) 44h
cert-manager cert-manager-startupapicheck-qs985 0/1 Completed 0 43h
cert-manager cert-manager-webhook-5976fbd9bd-5b2wm 1/1 Running 1 (55m ago) 44h
default kuard-7b5bffcc4f-8nfzs 1/1 Running 1 (55m ago) 16h
default kuard-7b5bffcc4f-fdz52 1/1 Running 1 (55m ago) 16h
default kuard-7b5bffcc4f-zldsc 1/1 Running 1 (55m ago) 16h
default metallb-controller-c55c89d-x27dm 1/1 Running 2 (52m ago) 12h
default metallb-speaker-82tlm 1/1 Running 2 (54m ago) 12h
default metallb-speaker-pljmf 1/1 Running 2 (54m ago) 12h
default my-harbor-chartmuseum-8c675ccd5-hj5fn 1/1 Running 1 (55m ago) 13h
default my-harbor-core-75d6fdb5c5-ngndb 1/1 Running 1 (55m ago) 13h
default my-harbor-database-0 1/1 Running 1 (55m ago) 13h
default my-harbor-jobservice-7cc857bcd8-zghvh 1/1 Running 1 (55m ago) 13h
default my-harbor-notary-server-85976c94b7-7jlkx 1/1 Running 2 (53m ago) 13h
default my-harbor-notary-signer-b9fcb9fb9-pd9bl 1/1 Running 2 (53m ago) 13h
default my-harbor-portal-8687f7fc88-cdtsm 1/1 Running 1 (55m ago) 13h
default my-harbor-redis-0 1/1 Running 1 (55m ago) 13h
default my-harbor-registry-5b7b77c57f-p6c4z 2/2 Running 2 (55m ago) 13h
default my-harbor-trivy-0 1/1 Running 1 (55m ago) 13h
default quickstart-ingress-nginx-controller-59898bff87-97md6 1/1 Running 1 (55m ago) 39h
kube-system coredns-6d8c4cb4d-gpf9w 1/1 Running 1 (55m ago) 10d
kube-system coredns-6d8c4cb4d-j6fzs 1/1 Running 1 (55m ago) 10d
kube-system etcd-master 1/1 Running 2 (55m ago) 10d
kube-system kube-apiserver-master 1/1 Running 2 (55m ago) 10d
kube-system kube-controller-manager-master 1/1 Running 2 (55m ago) 10d
kube-system kube-proxy-c4vjp 1/1 Running 1 (55m ago) 10d
kube-system kube-proxy-g7w9q 1/1 Running 1 (55m ago) 10d
kube-system kube-scheduler-master 1/1 Running 2 (55m ago) 10d
kube-system metrics-server-c56db8448-frlwp 1/1 Running 2 (52m ago) 9d
tigera-operator tigera-operator-59d6fdcd79-hmblx - Now you can access harbor via ingress nginx
externalIP.