1. Creation of Kubernetes Auth Method for 1001-myapp project
1.1 Getting the kube-apiserver Service Example
echo "https://$(kubectl get service kubernetes -o jsonpath='{.spec.clusterIP}'):443"
#https://192.168.194.129:443
1.2 Getting the Kubernetes CA Example
kubectl config view --minify --flatten -o jsonpath='{.clusters[0].cluster.certificate-authority-data}' | base64 -d
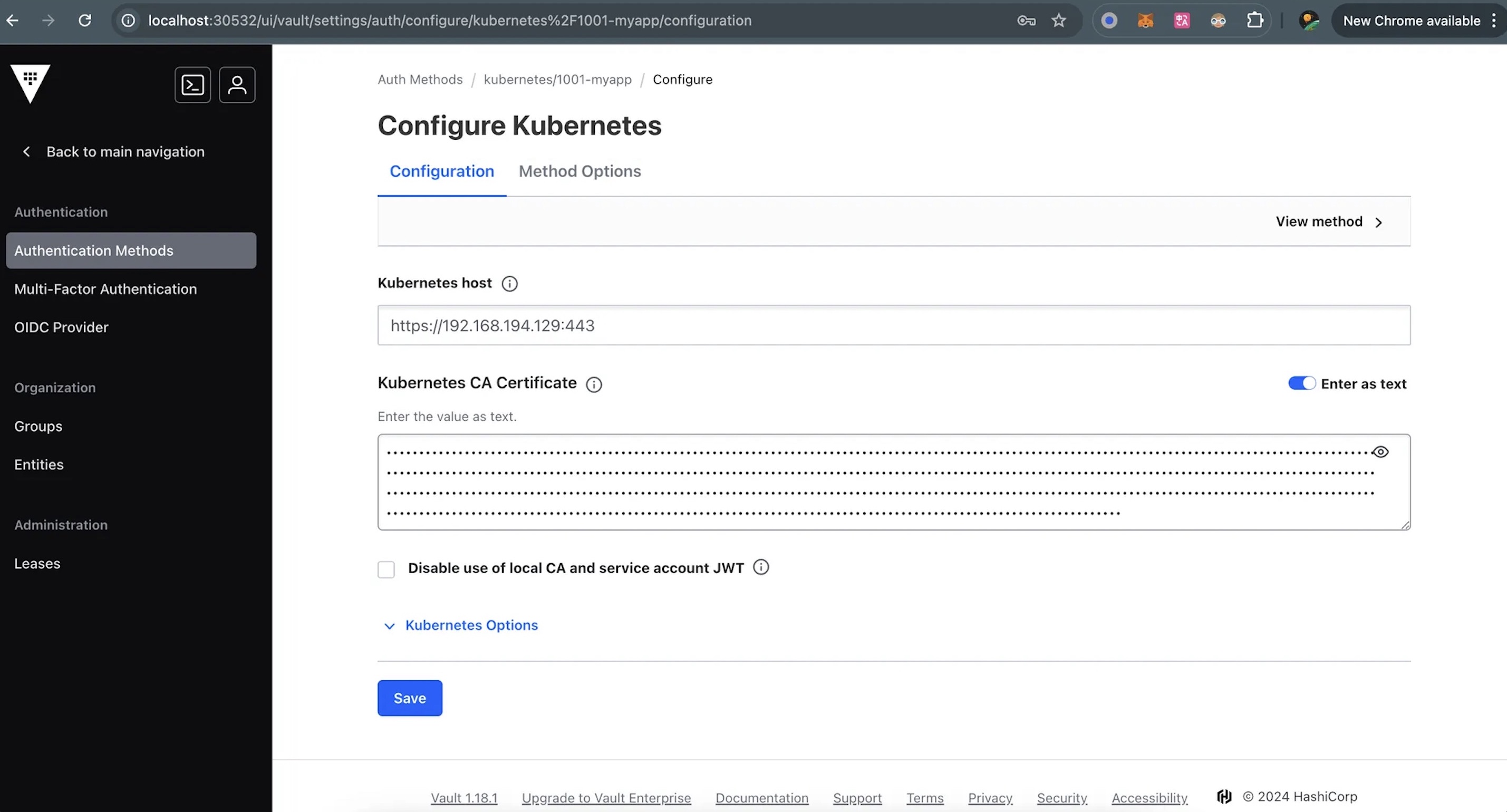
1.3 Create the Kubernetes Authentication
- 注:Vault UI 这里启用的 Kubernetes 类型认证路径为
kubernetes/1001-myapp,但对应 agent 那边业务 Pod 的 Annotation 配置 vault.hashicorp.com/auth-path 必须为 auth/kubernetes/1001-myapp

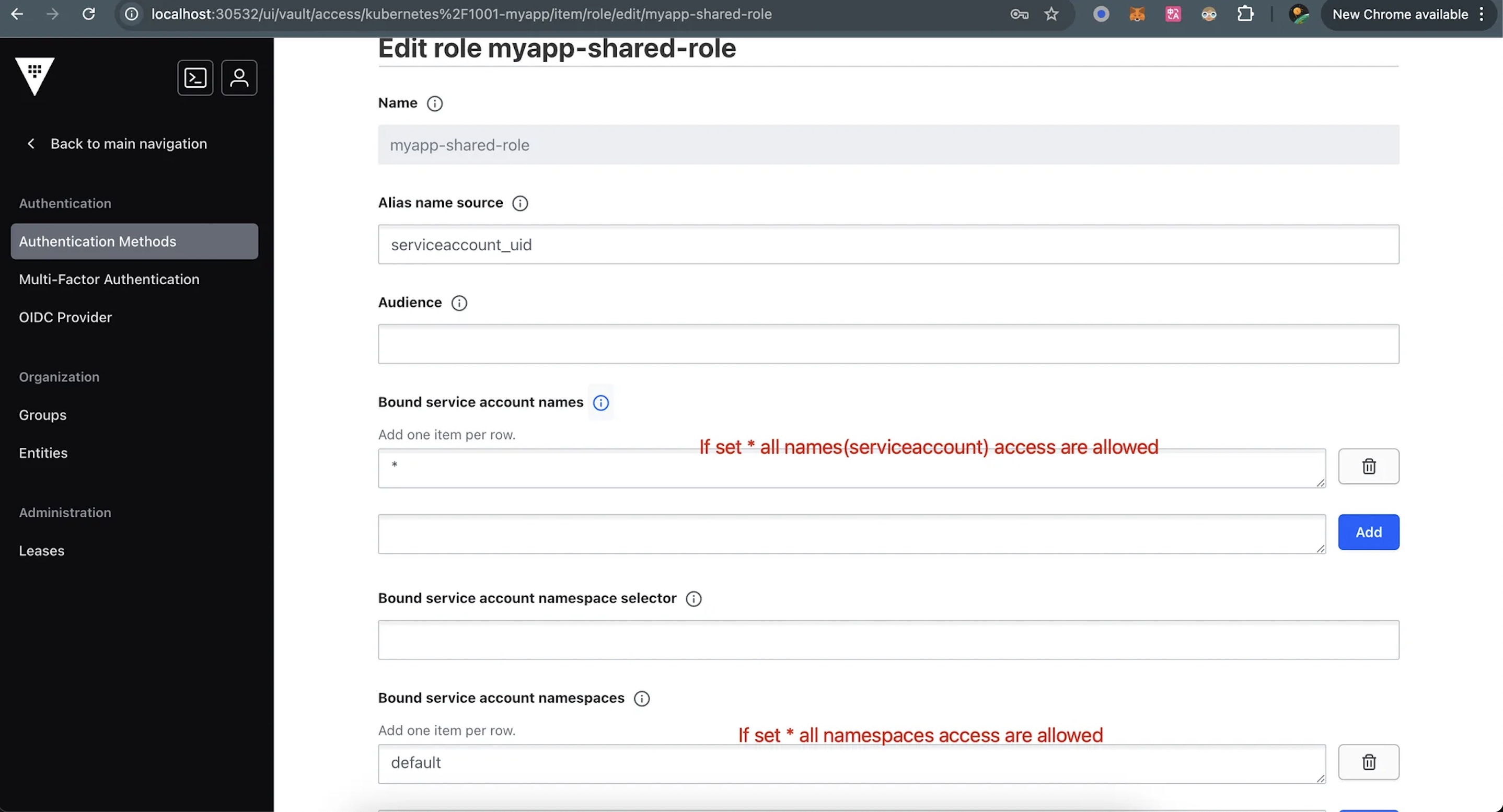
1.4 Add Access Role of Kubernetes Authentication
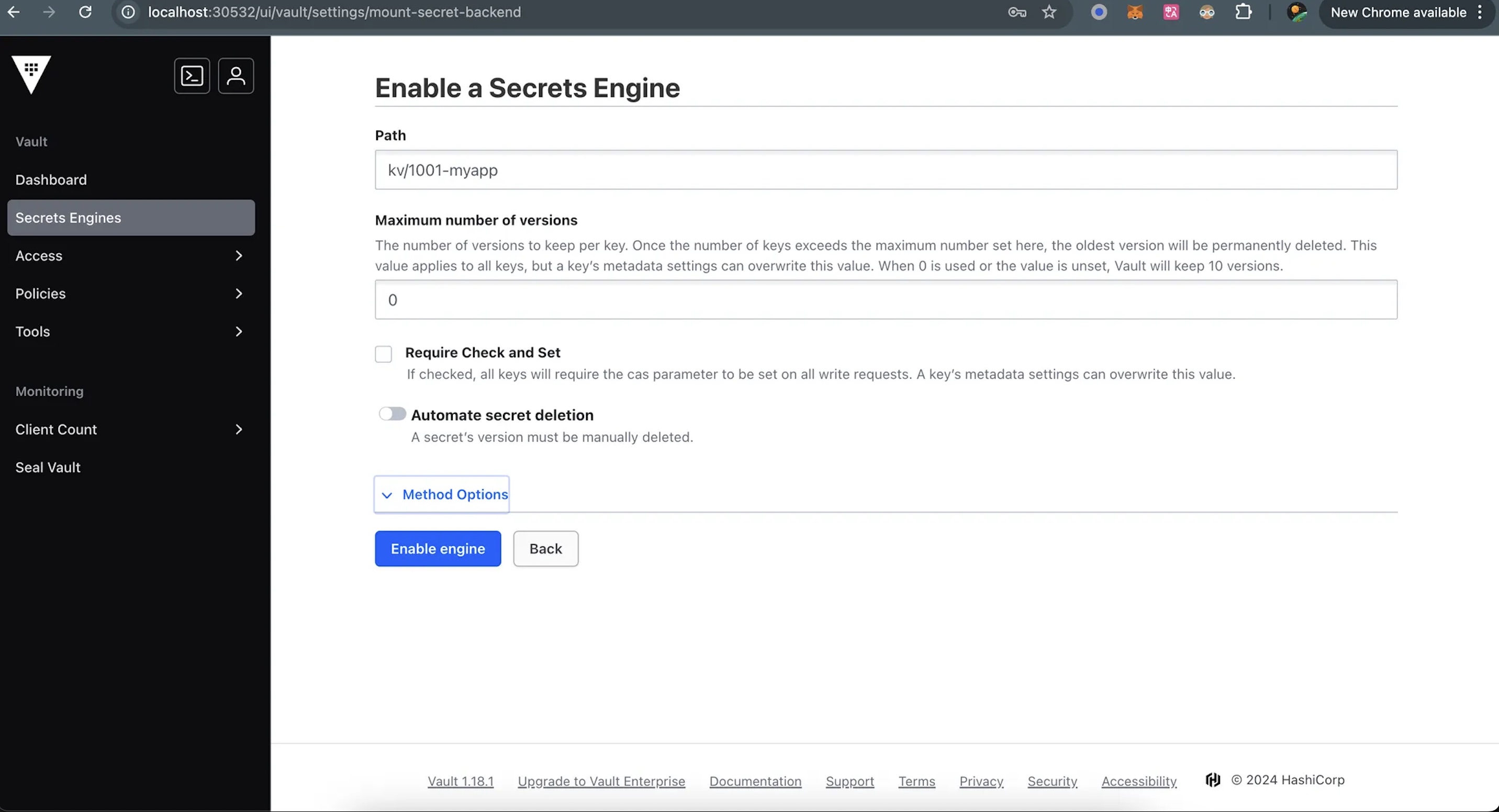
2. Creation of kv Secret Engine for 1001-myapp project
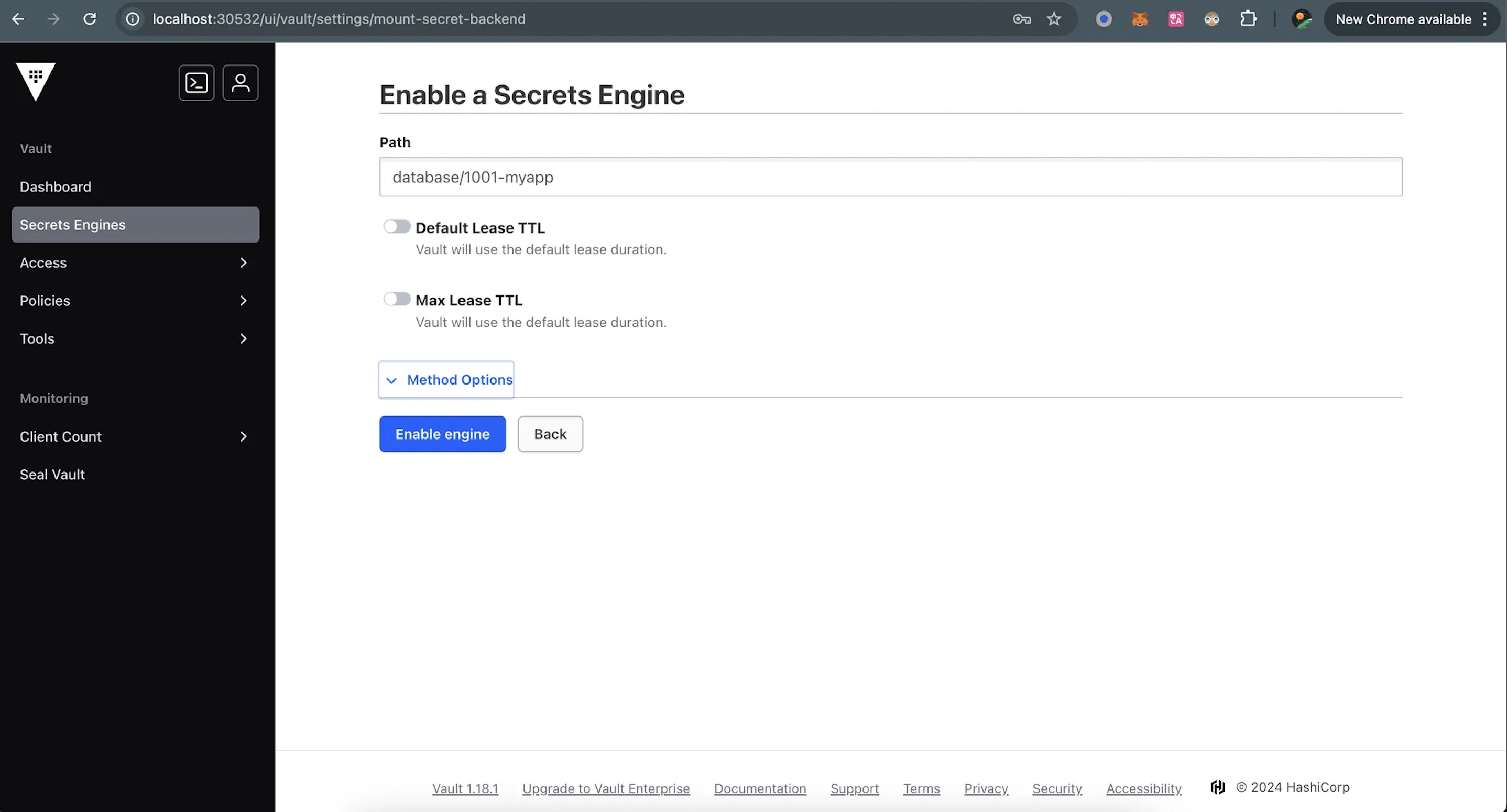
2.1 Enable a Secrets Engine
2.2 Add the Redis Secrets
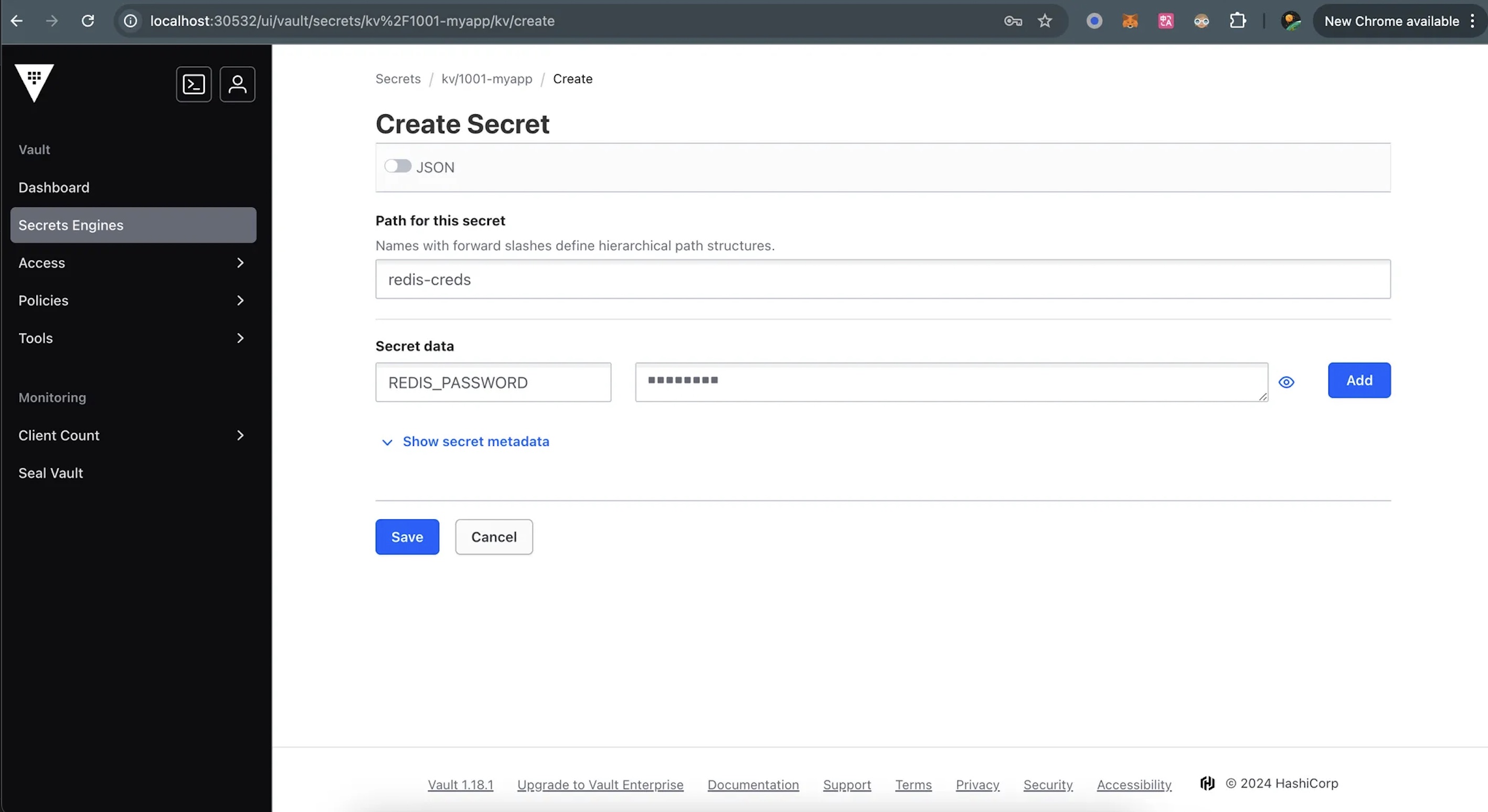
3. Creation of database Secret Engine for 1001-myapp project
3.1 Enable a Secret Engine
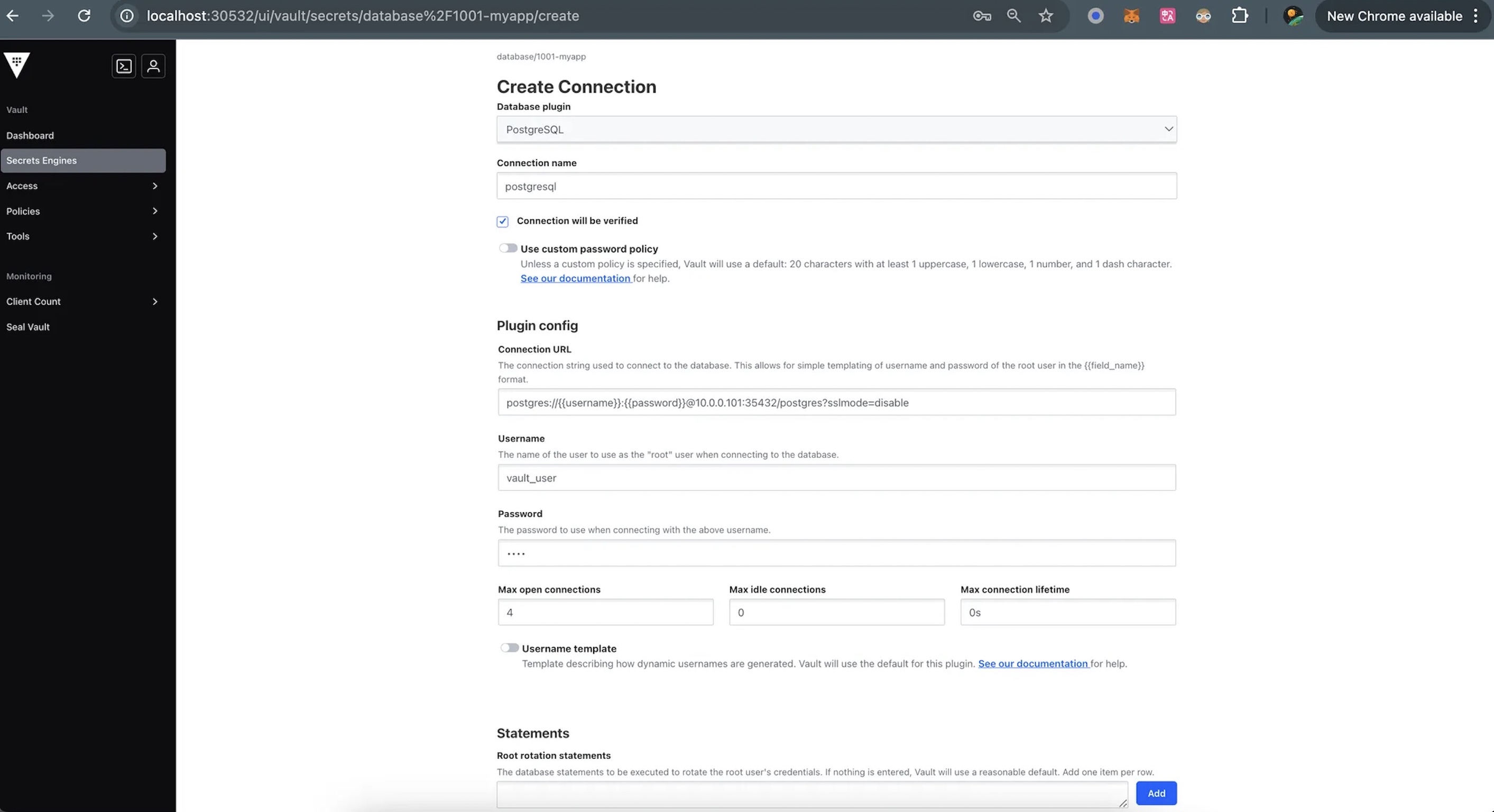
3.2 Add the PostgreSQL Connection
postgres://{{username}}:{{password}}@10.0.0.101:35432/postgres?sslmode=disable
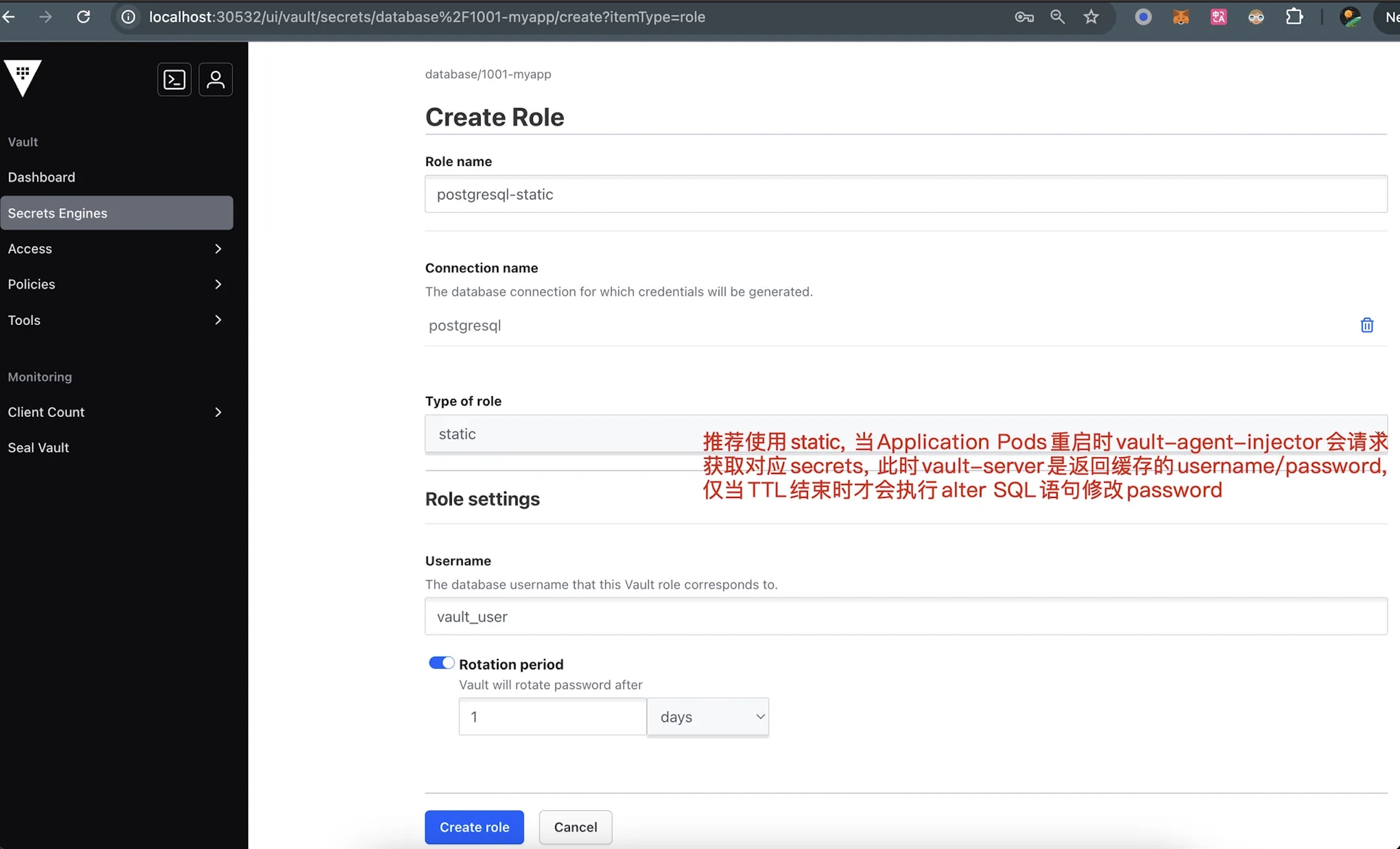
3.3 Add the Access Role of PostgreSQL Connection
Type of role: dynamic
- 不建议使用,因为应用 Pod 每次重启即 vault-agent 读取时,valut-server 都会执行 SQL 创建用户(如
v-root-postgres-YJHMS2hgaCnPFY66OTvg-1732417427), 虽然会在 TTL 后删除,但任然存在创建大量 PG 用户的风险。

- Equlevent to Create the dynamic role by Vault CLI
kubectl -n vault-system exec -ti vault-0 -- sh
export VAULT_TOKEN='hvs.tpsp0fqKX6weEqy3d0sOpgsh'
# Setup the allowed roles. (Note: Will auto update the PG user 'vault_user' to hash password)
vault write database/1001-myapp/config/postgresql \
allowed_roles="postgresql-dynamic" \
plugin_name="postgresql-database-plugin" \
connection_url="postgres://{{username}}:{{password}}@10.0.0.101:35432/postgres?sslmode=disable" \
username="vault_user" \
password="123456"
#Success! Data written to: database/1001-myapp/config/postgresql
# Create the dynamic role.
vault write database/1001-myapp/roles/postgresql-dynamic \
db_name=postgresql \
creation_statements="CREATE ROLE \"{{name}}\" WITH LOGIN PASSWORD '{{password}}' VALID UNTIL '{{expiration}}'; GRANT SELECT ON ALL TABLES IN SCHEMA public TO \"{{name}}\";" \
default_ttl='1h' \
max_ttl='24h'
# Check the getting configuration.
vault read database/1001-myapp/config/postgresql
#Key Value
#--- -----
#allowed_roles [postgresql-dynamic]
#connection_details map[backend:database/1001-myapp connection_url:postgres://{{username}}:{{password}}@10.0.0.101:35432/postgres?sslmode=disable max_connection_lifetime:0s max_idle_connections:0 max_open_connections:4 username:vault]
#password_policy n/a
#plugin_name postgresql-database-plugin
#plugin_version n/a
#root_credentials_rotate_statements []
#verify_connection true
# Check the getting dynamic role Metadata.
vault read database/1001-myapp/roles/postgresql-dynamic
#Key Value
#--- -----
#creation_statements [CREATE ROLE "{{name}}" WITH LOGIN PASSWORD '{{password}}' VALID UNTIL '{{expiration}}'; GRANT SELECT ON ALL TABLES IN SCHEMA public TO "{{name}}";]
#credential_type password
#db_name postgresql
#default_ttl 1h
#max_ttl 24h
#renew_statements []
#revocation_statements []
#rollback_statements []
# Check the getting dynamic role Password.
vault read database/1001-myapp/creds/postgresql-dynamic
#Key Value
#--- -----
#lease_id database/1001-myapp/creds/postgresql-dynamic/G8p9hvzU4VAjiv8Nj0O5cLgb
#lease_duration 1h
#lease_renewable true
#password 6T8G-FXuSiZlgb1WBMqb
#username v-root-postgres-YJHMS2hgaCnPFY66OTvg-1732417427
- Equlevent to Create the static role by Vault CLI
kubectl -n vault-system exec -ti vault-0 -- sh
export VAULT_TOKEN='hvs.tpsp0fqKX6weEqy3d0sOpgsh'
# Setup the allowed roles. (Note: Will auto update the PG user 'vault_user' to hash password)
vault write database/1001-myapp/config/postgresql \
allowed_roles="postgresql-static" \
plugin_name="postgresql-database-plugin" \
connection_url="postgres://{{username}}:{{password}}@10.0.0.101:35432/postgres?sslmode=disable" \
username="vault_user" \
password="123456"
#Success! Data written to: database/1001-myapp/config/postgresql
# Create the static role.
vault write database/1001-myapp/static-roles/postgresql-static \
db_name=postgresql \
rotation_statements="ALTER USER \"{{name}}\" WITH PASSWORD '{{password}}';" \
username="vault_user" \
rotation_period="24h"
# Check the getting configuration.
vault read database/1001-myapp/config/postgresql
#Key Value
#--- -----
#allowed_roles [postgresql-static]
#connection_details map[backend:database/1001-myapp connection_url:postgres://{{username}}:{{password}}@10.0.0.101:35432/postgres?sslmode=disable max_connection_lifetime:0s max_idle_connections:0 max_open_connections:4 username:vault]
#password_policy n/a
#plugin_name postgresql-database-plugin
#plugin_version n/a
#root_credentials_rotate_statements []
#verify_connection true
# Check the getting static role Metadata.
vault read database/1001-myapp/static-roles/postgresql-static
#Key Value
#--- -----
#credential_type password
#db_name postgresql
#last_vault_rotation 2024-11-23T17:22:40.814119366Z
#rotation_period 24h
#rotation_statements []
#username vault_user
# Check the getting static role Password.
vault read database/1001-myapp/static-creds/postgresql-static
#Key Value
#--- -----
#last_vault_rotation 2024-11-23T17:22:40.814119366Z
#password maSy-UDR9CPg46RpQ6lh
#rotation_period 24h
#ttl 23h41m50s
#username vault_user
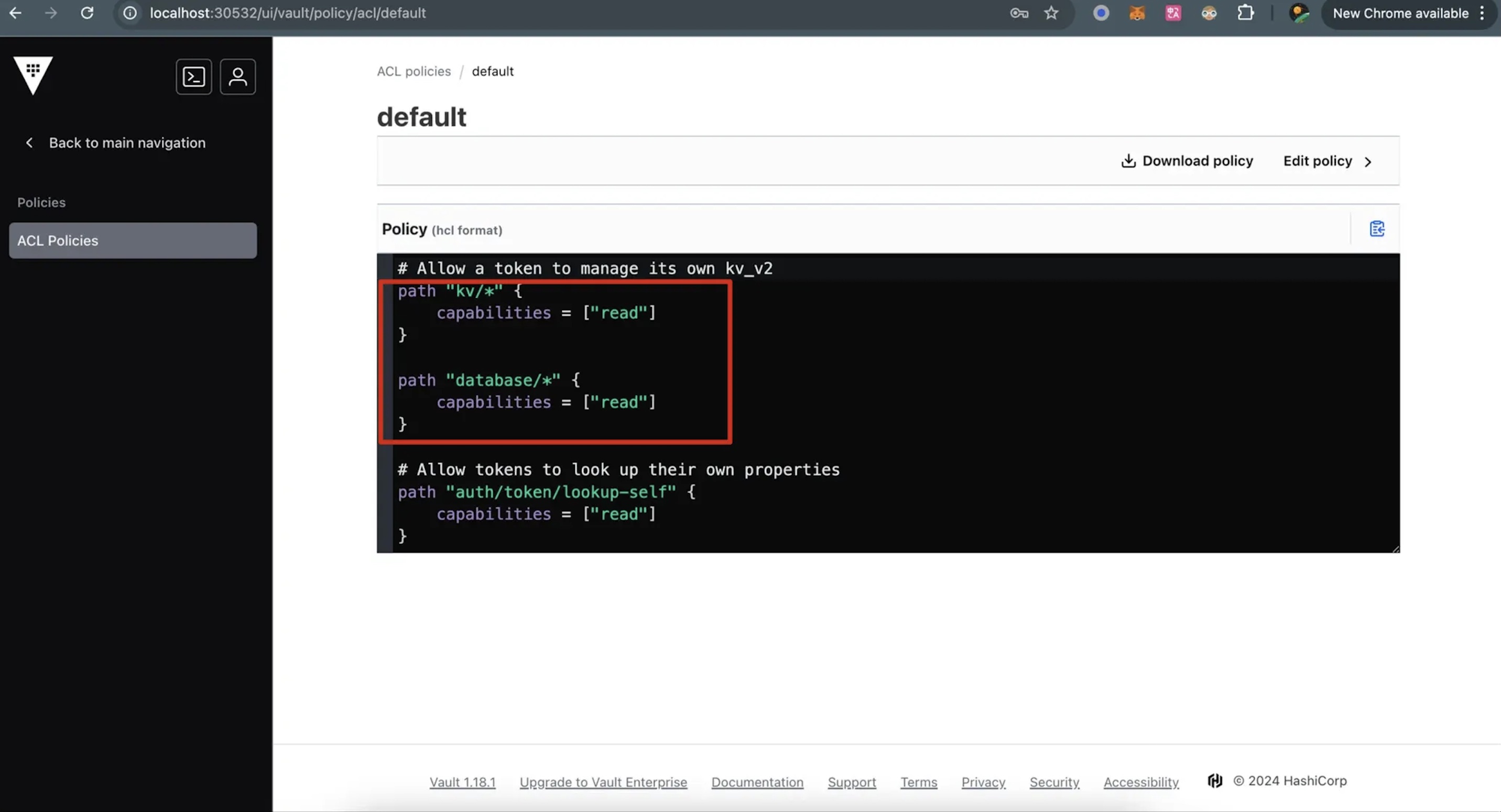
4. Configure of Policy
4.1 Modify the Default Policy